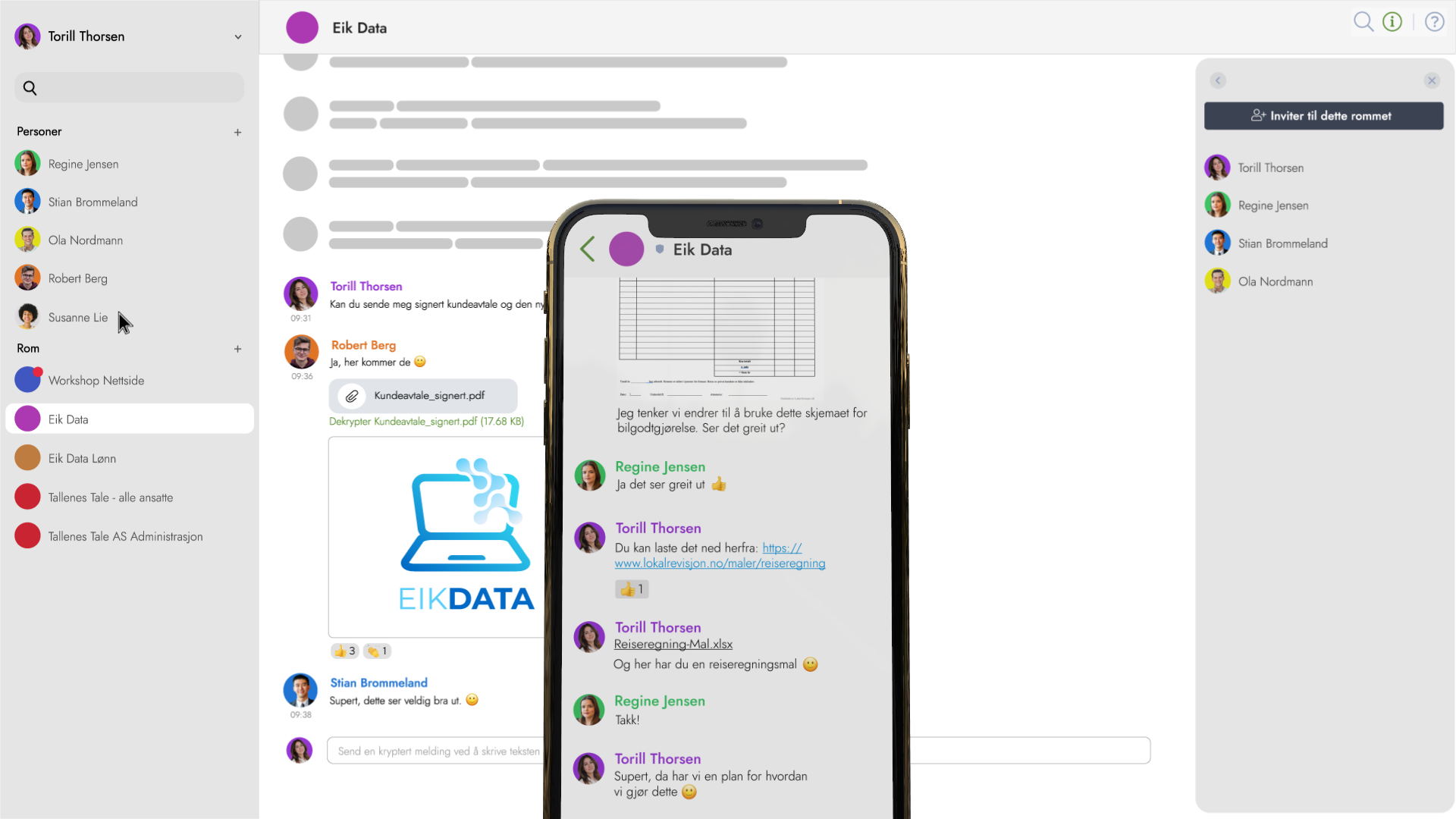
Innføringen av Verji har gitt en betydelig effektivisering og besparelse. Det som tidligere ble levert personlig eller via post går nå elektronisk, sier daglig leder Janne Eraker som bruker Verji på tredje året.
Hundrevis av bedrifter bruker Verji som sitt kommunikasjonsverktøy